
What Is Cybersecurity Mesh? Application and Advantages
Your data isn’t in one location in the modern business world. It is dispersed throughout sophisticated apps, mobile devices, distant offices, and cloud services. Every day, this digital environment becomes more expansive and dispersed. The issue? The majority of businesses continue to employ the antiquated castle-and-moat security model. Their main office is surrounded by a massive, robust wall, and once an attacker breaches it, they have complete access to the network. This is why many modern companies are now shifting toward Cybersecurity Mesh.
Presenting the cybersecurity mesh Architecture for Cybersecurity. It is the contemporary cybersecurity solutions KSA to safeguarding this vast digital empire. To put it simply, it is a method of transforming security from a single, centralized wall to a flexible, distributed net that safeguards each and every user, wherever they may be.
Table of Contents
The Problem with the Old Castle-and-Moat Model
First and foremost, it is vital to comprehend why the old model fails in the contemporary world.
In the traditional formation –
- The Castle – Your prime corporate data center or office building.
- The Moat – The huge protection perimeter developed to keep threats out.
This worked when all workers sat in the office and all applications were on-site.
Why it fails today –
1. Remote Work – Employees work from home, coffee shops, and various nations, sidestepping the moat properly.
2. The Cloud – Data and applications live in Amazon Web Services, Azure, and Google Cloud, outside the conventional network perimeter of the company.
3. IoT Devices – Smart devices, sensors, and functional technology are everywhere, usually launched without robust central security.
If a hacker successfully steals the password of an employee, they have efficiently crossed the moat and are now protectively inside the castle. From there, they can move easily, which is called lateral movement, and locate the most useful data.
What is Cybersecurity Mesh?

The Cybersecurity Mesh isn’t a single product; it is an architectural system, a way of developing protection that treats every user, every device, and each application as its own, separate protection perimeter. Imagine replacing the single, hefty castle wall with an adaptable, interlocking net of protection guidelines.
Core Components of the Mesh
The mesh has 3 major components that make it work –
1. The Distributed Security Controls (The Net)
Rather than one big firewall, the mesh places smaller, reliable security controls right next to the properties they are meant to secure.
A protection tool examines the user accessing a file in Dropbox, a distinct tool verifies the code functioning on an application server in the cloud, and another tool checks the gadget protection status prior to permitting a login. These managers are independent, yet cooperative.
2. Identity is the New Perimeter
In the mesh model, the question is not “are you inside our office network?” The question is “who are you, and what are you trying to enter?” Identity, the user or the device, becomes the most crucial protection check.
This is gained mainly through Zero Trust Network Access. Zero Trust means never trust, constantly examine. Even if a user logs in successfully, the system constantly checks their approvals and behavior.
3. Centralized Policy Management
With protection controls scattered everywhere, you require one brain to handle them. The mesh utilizes a centralized management layer to enforce protection guidelines constantly throughout all tools, services, and sites.
If the central guideline says “Finance records can only be accessed from company-granted laptops,” the mesh design makes sure that policy is enforced whether the user is in Saudi Arabia or elsewhere in the world.
The Applications of Cybersecurity Mesh
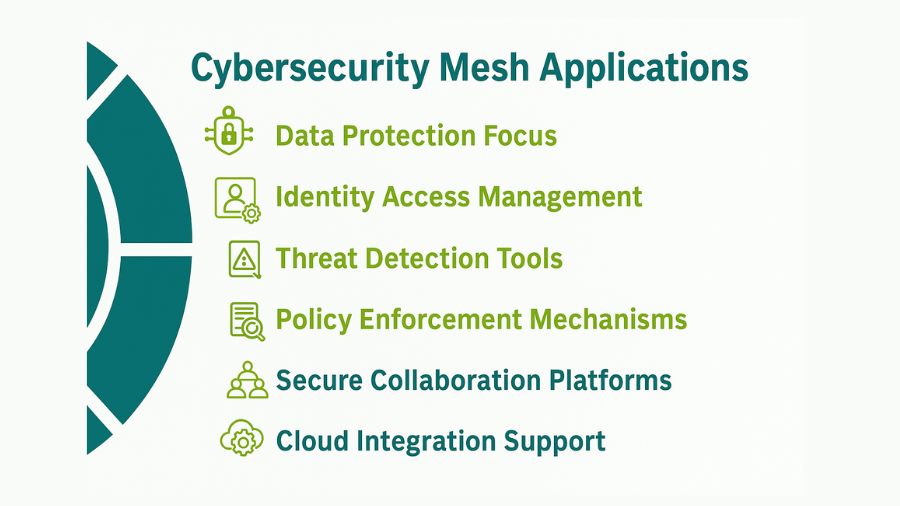
The adaptability of the mesh makes it ideal for resolving contemporary IT difficulties –
Application 1 – Hybrid and Multi-Cloud Environments
Most big corporations do not utilize only one cloud provider; they utilize two or three. Protection guidelines usually vary between clouds, creating gaps.
Mesh Solution – The mesh permits the central policy engine to communicate with protection tools in AWS, Azure, and your on-premises data center. This makes sure your data in all three sites is secured by the precise same regulations, delivering smooth cybersecurity services Saudi Arabia across any hosting environment.
Application 2 – Securing Remote Workers
When your workers connect from home, they do not undergo the old moat. They require security wherever they connect.
Mesh Solution – The mesh utilizes ZTNA to examine the user and the device health prior to giving access to particular applications. The security managements are applied directly to the connection of the user, not only to the office perimeter. If a user’s laptop is infected, the mesh isolates the device immediately, controlling the infection from spreading.
Application 3 – Governing IoT and Operational Technology
Factories, hospitals, and crucial infrastructure utilize millions of smart sensors. These devices are tough to patch and handle centrally.
Mesh Solution – The mesh isolates these devices into small, secure segments. A sensor handling a building’s air conditioning systems is segmented away from the corporate account network. If the sensor is compromised, the breach can’t impact the main business data.
Key Advantages of Adopting a Cybersecurity Mesh

Transitioning to this architecture delivers remarkable advantages that older models just can’t deliver –
1. Better Security and Reduced Risk –
- Stops Lateral Movement – Because every asset is secured individually, a hacker who compromises one system can’t effortlessly jump to another. The harm is contained instantly.
- Stronger Zero Trust – By changing the concentration from location to identity, you enforce a robust protection structure every single time a user accesses data.
2. Faster Innovation and Agility –
- Easier Cloud Adoption – The mesh permits organizations to adjust new cloud services and applications rapidly without having to rewrite or reconstruct the whole security structure from scratch. Security is baked in, not bolted on.
- Vendor Integration – It enables the integration of security items from several vendors instead of locking you into one monolithic supplier. This is a vital factor of high-level IT services in Saudi Arabia.
3. Improved User Experience –
- Seamless Access – For authorized users, the mesh delivers a seamless, more constant login experience, as the security checks occur transparently in the background, no matter where they are logging in from.
4. Simplified Compliance –
- Constant Policy Enforcement – With the central management layer, showing adherence to data rules becomes much easier because the policy is enforced everywhere simultaneously.
Conclusion
The conventional notion of a single, unbreakable security wall is no longer relevant. It no longer works because the world is too dispersed and complicated. The crucial advancement is the cybersecurity mesh, which substitutes an adaptable, intelligent network for a strict perimeter.
It’s a fundamental change that guarantees the individual protection of each user, device, and piece of data. The mesh is the future of robust and efficient cybersecurity for any contemporary company, including Bluechip Tech, wishing to safely use the cloud and remote work.
Also Read: What Is a Network Security Audit & Why Does It Matter?









